politics and politicians
See other politics and politicians Articles
Title: Hillary Clinton's Private E-Mail Draws Scrutiny Hacker "Guccifer" first discovered backchannel receipt of intel info
Source:
[None]
URL Source: http://www.thesmokinggun.com/docume ... -private-e-mail-account-897531
Published: Mar 4, 2015
Author: Staff
Post Date: 2015-03-04 04:28:33 by out damned spot
Keywords: Hillary, email
Views: 2921
Comments: 21
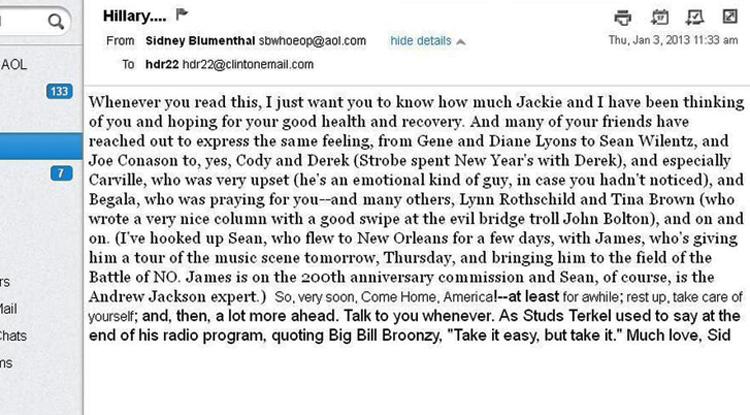
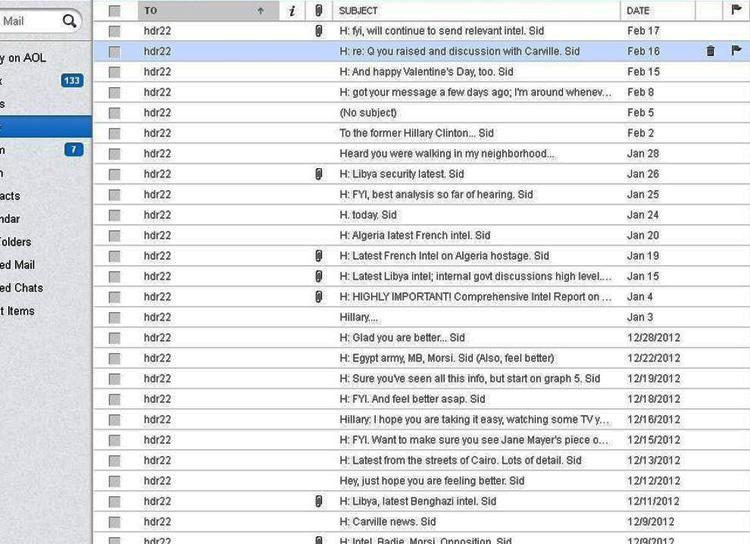
MARCH 3--The disclosure that Hillary Clinton used a non-governmental e-mail address while she was Secretary of State originally came courtesy of “Guccifer,” the Romanian hacker now serving time in a Bucharest prison for his online attacks against scores of public figures. As TSG first reported in March 2013, “Guccifer” illegally accessed the AOL e- mail account of Sidney Blumenthal, who worked as a senior White House adviser to President Bill Clinton, and later became a senior adviser to Hillary Clinton’s 2008 presidential campaign. When “Guccifer” (who was later identified as Marcel Lazar Lehel) breached Blumenthal’s account, he discovered an assortment of correspondence sent to Hillary Clinton at the e-mail address hdr22@clintonemail.com. The “clintonemail.com” domain was registered in 2009, shortly after her nomination to become Secretary of State. While Blumenthal, a longtime Hillary Clinton confidant, used her private e-mail to send personal messages (like a get well note after she fell at home and suffered a concussion in December 2012), he also forwarded the Cabinet member a series of “Confidential” memos about foreign policy matters. The “For: Hillary, From: Sid” memos, provided to TSG by “Guccifer,” address a wide range of topics in global flashpoints like Algeria, Turkey, Mali, and Libya. Blumenthal also provided Clinton with information about the European Central Bank, the Georgia elections, and German Chancellor Angela Merkel. The memos to Clinton carried titles like “Comprehensive Intel Report on Libya,” and included all-cap warnings that, “THE FOLLOWING INFORMATION COMES FROM EXTREMELY SENSITIVE SOURCES AND SHOULD BE HANDLED WITH CARE.” Blumenthal has not held a public post since leaving his White House job in January 2001. Each memo included a note on the sources of intelligence included in the document. One typical memo referred to “Sources with access to the highest levels of the Muslim Brotherhood in Egypt, the leadership of the Armed Forces, and Western Intelligence, diplomatic, and security services.” A January 15, 2013 memo on “Libya internal government discussion,” reportedly relied on “Sources with direct access to the Libyan National Government.” The memos offer no indication as to whether the intelligence gathered by Blumenthal was done at Clinton’s suggestion. Likewise, the hacked material does not include evidence of Clinton’s response to Blumenthal’s memos (which appear to have been prepared with input from Tyler Drumheller, a former Central Intelligence Agency official who ran covert operations in Europe). While he rummaged through Blumenthal’s e-mail account, “Guccifer” sorted mail sent to Clinton’s hdr22@clintonemail.com address. He then took a screen grab showing more than two dozen e-mails sent over a two-month period ending in mid- February 2013. Along with Valentine’s Day greetings and a mention of Clinton “walking in my neighborhood,” the subject lines of those Blumnethal e-mails include repeated references to “intel” shared with the Secretary of State. Other subject lines refer to “Q you raised” and “got your message a few days ago; I’m around whenev…” A February 17 e-mail included the subject line, “H: fyi, will continue to send relevant intel. Sid.” (4 pages)
Poster Comment: Screen shot: 

Post Comment Private Reply Ignore Thread
Top • Page Up • Full Thread • Page Down • Bottom/Latest
#1. To: out damned spot (#0)
Those attachments are very damning. This was a server run by the Xlintons. Secure info on it could have been (and was) obtained by hackers and hostile foreign powers. How do we know that Hitlery's server was not compromised and it led to the deaths of Americans or others or compromising the intel assets or leaking official secrets to an enemy? Hitlery had a sworn duty to follow our security protocols and that her messaging be protected by security professionals.
What are the chances that the intel reports held classified information?
When Hillary Clinton ceased to be Secretary of State, the official records she retained were removed from agency custody and became alienated. (44 U.S. Code § 3105) The records are not available to the agency for conducting business. The records have not been provided to the Archivist. For classified intel, think David Petraeus or Bradley/Chelsea Manning. https://www.law.cornell.edu/uscode/text/44/3101 The head of each Federal agency shall make and preserve records containing adequate and proper documentation of the organization, functions, policies, decisions, procedures, and essential transactions of the agency and designed to furnish the information necessary to protect the legal and financial rights of the Government and of persons directly affected by the agency’s activities. https://www.law.cornell.edu/uscode/text/44/3105 The head of each Federal agency shall establish safeguards against the removal or loss of records he determines to be necessary and required by regulations of the Archivist. Safeguards shall include making it known to officials and employees of the agency— (1) that records in the custody of the agency are not to be alienated or destroyed except in accordance with sections 3301–3314 of this title, and (2) the penalties provided by law for the unlawful removal or destruction of records. https://www.law.cornell.edu/uscode/text/44/3106 The head of each Federal agency shall notify the Archivist of any actual, impending, or threatened unlawful removal, defacing, alteration, or destruction of records in the custody of the agency of which he is the head that shall come to his attention, and with the assistance of the Archivist shall initiate action through the Attorney General for the recovery of records he knows or has reason to believe have been unlawfully removed from his agency, or from another Federal agency whose records have been transferred to his legal custody. In any case in which the head of the agency does not initiate an action for such recovery or other redress within a reasonable period of time after being notified of any such unlawful action, the Archivist shall request the Attorney General to initiate such an action, and shall notify the Congress when such a request has been made. http://www.archives.gov/about/laws/fed-agencies.html National Archives Records Management by Federal Agencies (44 U.S.C. Chapter 31) The head of each Federal agency shall make and preserve records containing adequate and proper documentation of the organization, functions, policies, decisions, procedures, and essential transactions of the agency and designed to furnish the information necessary to protect the legal and financial rights of the Government and of persons directly affected by the agency’s activities. - - - The head of each Federal agency shall establish and maintain an active, continuing program for the economical and efficient management of the records of the agency. The program, among other things, shall provide for (1) effective controls over the creation and over the maintenance and use of records in the conduct of current business; (2) cooperation with the Archivist in applying standards, procedures, and techniques designed to improve the management of records, promote the maintenance and security of records deemed appropriate for preservation, and facilitate the segregation and disposal of records of temporary value; and (3) compliance with sections 2101-2117, 2501-2507, 2901-2909, and 3101-3107, of this title and the regulations issued under them. - - - When the head of a Federal agency determines that such action may affect substantial economies or increased operating efficiency, the head of such agency shall provide for the transfer of records to a records center maintained and operated by the Archivist, or, when approved by the Archivist, to a center maintained and operated by the head of the Federal agency. - - - An official of the Government who is authorized to certify to facts on the basis of records in such official’s custody, may certify to facts on the basis of records that have been transferred by such official or such official’s predecessors to the Archivist, and may authorize the Archivist to certify to facts and to make administrative determinations on the basis of records transferred to the Archivist, notwithstanding any other law. - - - The head of each Federal agency shall establish safeguards against the removal or loss of records the head of such agency determines to be necessary and required by regulations of the Archivist. Safeguards shall include making it known to officials and employees of the agency-- (1) that records in the custody of the agency are not to be alienated or destroyed except in accordance with sections 3301-3314 of this title, and (2) the penalties provided by law for the unlawful removal or destruction of records. - - - (a) FEDERAL AGENCY NOTIFICATION.—The head of each Federal agency shall notify the Archivist of any actual, impending, or threatened unlawful removal, defacing, alteration, corruption, deletion, erasure, or other destruction of records in the custody of the agency, and with the assistance of the Archivist shall initiate action through the Attorney General for the recovery of records the head of the Federal agency knows or has reason to believe have been unlawfully removed from that agency, or from another Federal agency whose records have been transferred to the legal custody of that Federal agency. (b) ARCHIVIST NOTIFICATION.—In any case in which the head of the Federal agency does not initiate an action for such recovery or other redress within a reasonable period of time after being notified of any such unlawful action described in subsection (a), or is participating in, or believed to be participating in any such unlawful action, the Archivist shall request the Attorney General to initiate such an action, and shall notify the Congress when such a request has been made. - - - Chapters 21, 25, 27, 29, and 31 of this title do not limit the authority of the Comptroller General of the United States with respect to prescribing accounting systems, forms, and procedures, or lessen the responsibility of collecting and disbursing officers for rendition of their accounts for settlement by the General Accounting Office. = = = = = = = = = http://www.archives.gov/records-mgmt/bulletins/2011/2011-03.html National Archives and Records Administration (NARA) December 22, 2010 TO: Heads of Federal agencies SUBJECT:Guidance Concerning the use of E-mail Archiving Applications to Store E-mail EXPIRATION DATE: November 30, 2013 1. What is the purpose of this bulletin? This bulletin is a re-issuance of NARA Bulletin 2008-5, Guidance concerning the use of e-mail archiving applications to store e-mail. The guidance issued in 2008-05 remains unchanged with the exception of minor editorial changes, changes to the expiration date, and references to the Code of Federal Regulations (CFR) found in the bulletin. The bulletin provides guidance to Federal agencies on using e-mail archiving applications and similar technologies for managing e-mail records. It advises agencies that: If an agency decides to use e-mail archiving applications to manage Federal records the agency is responsible for addressing those areas where the applications do not meet the requirements of the Federal Records Act and applicable NARA regulations. 2. What is e-mail archiving? E-mail archiving generally refers to applications that remove e-mail from the mail server and manage it in a central location also known as an archive. Information technology professionals use the term "archiving" to mean the copying or transfer of files for storage. In general, these applications collect in a central repository the e-mail (which may include attachments, calendars, task lists, etc.) of some or all agency users. E-mail archiving applications typically require little to no action on the part of the user to store or manage the e-mail records. Once messages are stored, authorized users are able to search the repository. 3. What is the status of e-mail messages as Federal records? E-mail messages are records when their content (including attachments) meets the definition of a record under the Federal Records Act. See also 36 CFR 1236, and specifically 36 CFR 1236.22, which provides additional requirements for electronic mail. 4. What are the requirements for managing e-mail messages as Federal records? Recordkeeping systems that include electronic mail messages must: Permit easy and timely retrieval of both individual records and files or other groupings of related records; Retain the records in a usable format for their required retention period as specified by a NARA-approved records schedule; Be accessible by individuals who have a business need for information in the system; Preserve the transmission and receipt data specified in agency instructions; and Permit transfer of permanent records to the National Archives and Records Administration (see 36 CFR 1235.44 - 1235.50 and 36 CFR 1236.20). [...] 10. Where do I go for more information? If you need general information about the contents of this bulletin, please contact ERM@nara.gov. DAVID S. FERRIERO
Don't get your hopes up. She will look right into the camera a arrogantly state that she did not have sexwill relations with those emails and that she never aksed anyone to lie. And guess what.........all of the MSM will swear to it.
потому что Бог хочет это тот путь
- - - - - - Note: Hillary left office February 1, 2013 - - - https://en.wikipedia.org/wiki/Guccifer Guccifer (real name Marcel Lazar Lehel) is a Romanian hacker who is responsible for a number of high-level security breaches involving both current and former members of the United States government. The hacker first appeared in news media in February, 2013 after The Smoking Gun reported he was responsible for hacking the AOL account of Dorothy Bush Koch, sister of former president George W. Bush. Family photos of former president George H. W. Bush, who was in the hospital at the time, were circulated to the internet. He also circulated a self-portrait painted by George W. Bush, depicting the former president taking a shower. Guccifer has gone on to hack a number of AOL, Yahoo, Flickr and Facebook accounts, giving him access to information about current and former high-level government officials. In January 2014 he was jailed in his native Romania for seven years for hacking emails of Romanian officials including the head of the Romanian Intelligence Service. Hacking of politicians' accounts Guccifer later hacked Colin Powell's website and accessed years worth of his correspondence from another AOL account. The correspondence included personal financial information as well as e-mails to George Tenet, Richard Armitage, and John Negroponte. The hacker also targeted U.S. Senator Lisa Murkowski, a senior UN Official, members of the Rockefeller family, former FBI and Secret Service agents, as well as the brother of Barbara Bush, CBS sportscaster Jim Nantz, and former Miss Maine Patricia Legere. On March 20, 2013, USA Today reported that Guccifer had successfully hacked the e-mail account of former aide to president Bill Clinton, Sidney Blumenthal. He distributed private memos sent to Secretary of State Hillary Clinton involving recent events in Libya, including the September 11, 2012 Benghazi attack. Before distributing the memos, he copied and pasted the text into his own new documents, then reformatted them with pink backgrounds and comic sans font.The hacker's IP address was traced to Russia, however there was no certainty as to whether this was his actual location or whether he had used a proxy to hide his true location. In early May 2013, Guccifer hacked into online accounts owned by two members of the Council on Foreign Relations, as well as accounts owned by Adam Posen and his wife and another owned by a former Federal Reserve Board official. [snip]
Hillary ain't Bill.
You are right. She has bigger balls.
потому что Бог хочет это тот путь
Nice sleuthing. The statute is lacking in serious penalties, it seems.
https://twitter.com/HillaryClinton/status/573340998287413248 Hillary Clinton Examined for Clintonian tendencies, questions arise: Hillary Clinton left the State Department on February 1, 2013. UNCLASSIFIED (U) U.S. Department of State Foreign Affairs Manual, Volume 12, Diplomatic Security 12 FAM 530 Page 1 of 49 UNCLASSIFIED (U) 12 FAM 530 (CT:DS-229; 02-25-2015) (Office of Origin: DS/SI/IS) NOTE: In September, 2013, DS provided new guidance that rescinded some information still existing in this subchapter. This subchapter will be revised to reflect the new guidance – Refer to Department Notice 2013_09_168 for more information. [excerpts - all dated before Hillary Clinton left the State Department] (CT:DS-185; 01-31-2012) (Uniform State, USAID, OPIC, TDP) a. When departing a post upon transfer, resignation, or retirement, each employee, irrespective of rank, must certify as part of the post clearance procedure that: (1) They are not taking classified material from the post through any other than authorized means; (2) Such material is not in their household or personal effects; and (3) Such material will not be mailed or otherwise transmitted in violation of 12 FAM 536.10. b. Within USAID, provide certification on Form SF-312, Classified Information Nondisclosure Agreement, for employees and contractors with access to classified information. - - - - - (CT:DS-157; 05-14-2010) (Uniform State, USAID, OPIC, TDP) a. A person must only be given access to classified information when a favorable determination has been made as to the person’s trustworthiness. The determination of trustworthiness, referred to as a security clearance, is based on such investigations as may be required in accordance with the applicable standards and criteria. b. DS/SI/PSS keeps a record of all security clearances for Department of State employees and contractors. USAID/SEC keeps a record of security clearances for USAID personnel. Special and specifically authorized clearances are required for access to information identified as Restricted Data, NATO, COSMIC, cryptographic, intelligence, and other information given special protection by law or regulation. - - - - - (CT:DS-157; 05-14-2010) (Uniform State, USAID, OPIC, TDP) A person is not entitled to receive classified information solely by virtue of official position or by virtue of having been granted a security clearance. A person must also have a need for access to the particular classified information sought in connection with the performance of official U.S. Government duties or contractual obligations, or as otherwise specifically authorized by these regulations. The officers having responsibility for the classified information must make the determination of that need. - - - - - (CT:DS-157; 05-14-2010) (Uniform State, USAID, OPIC, TDP) For the Department, former Presidential appointees may apply to the Office of Freedom of Information, Privacy and Classification Review to the Office of Information Programs and Services, (A/GIS/IPS) for access to those documents which they originated, reviewed, signed, or received while serving as Presidential appointees, provided that all of the following conditions are satisfied: (1) DS/SI/PSS makes the determination that granting access to the intended recipient is consistent with the interests of national security and that the intended recipient is trustworthy. Access will be limited to categories of information over which the agency has classification jurisdiction; (2) The intended recipient agrees in writing to safeguard the information from unauthorized disclosure in a manner consistent with applicable statutes and regulations; (3) The intended recipient agrees in writing to authorize the review of notes and manuscripts for the purpose of determining that no classified information is contained therein; (4) The intended recipient agrees in writing that the information involved will not be further disseminated without the express permission of the agency; (5) The information requested is reasonably accessible and can be located and compiled with a reasonable amount of effort. Otherwise, A/GIS/IPS will charge fees to assemble the information, in accordance with the schedule in 22 CFR 171.6; (6) Any individual or research assistant requiring access on behalf of the intended recipient must also meet all of the above conditions. Such personal assistants must be authorized to be working for the former appointee exclusively and not gathering information for publication on their own; (7) Information compiled by research assistants is similarly subject to all conditions enumerated above; and (8) Upon request, such information as the recipient may identify will be reviewed for declassification in accordance with the provisions of these regulations. - - - - - (CT:DS-157; 05-14-2010) (Uniform State, USAID, OPIC, TDP) a. Provision of classified information to individuals or organizations of the Federal Government outside the Executive Branch will be determined on a case-by-case basis by the Office of Freedom of Information, Privacy and Classification Review (A/GIS/IPS) in coordination with other concerned bureaus, including H and L; in OPIC by the Director of Public Affairs; and in USAID by the Bureau for Legislative Affairs, Congressional Liaison Staff. b. Subject to the above paragraph and 12 FAM 536.2 and 12 FAM 536.3, classified material will not normally be provided to persons outside the Executive Branch of the U.S. Government. However, exceptions may be made provided that all the conditions in 12 FAM 536.2 are satisfied. - - - - - (CT:DS-157; 05-14-2010) (Uniform State, USAID, OPIC, TDP) a. Information contained in intelligence documents, including those produced by the Bureau of Intelligence and Research (INR), that is marked with specific control markings must be handled within the framework of the limitations imposed by such controls. For details and definitions of these controls, refer to 11 FAM. Failure to comply with these provisions will be considered a violation to be handled as prescribed under subchapter 12 FAM 550. b. Information bearing the notation “WARNING NOTICE-INTELLIGENCE SOURCES OR METHODS INVOLVED” must not be disseminated in any manner outside authorized channels without the permission of the originating agency and an assessment by the senior intelligence official in the disseminating agency as to the potential risks to the national security and to the intelligence sources and methods involved. c. In general, employees must clear with INR/DOC/OIL/CS telegrams and other documents originating in the Department of State which include or refer to classified intelligence information. - - - - - (CT:DS-157; 05-14-2010) (Uniform State, USAID, OPIC, TDP) a. Classified information must not be used for personal interests of any employee and must not be entered in personal diaries or other non-official records. b. Employees must not hold discussions of classified information in the presence or hearing of persons who are not authorized to have knowledge thereof. c. Employees must not discuss classified information in conversations on nonsecure telephones or office intercoms. - - - - - STATE DEPARTMENT, 12 FAM 530, Storing and Safeguarding Classified Material
Does anyone else find it bizarre that the Fed can find racist emails in the Ferguson Police Dpet. lickety split but no-one can find the Sec. of State's emails for years?
потому что Бог хочет это тот путь
David Petraeus recently pleaded guilty to this criminal offense. Note that what he pleaded guilty to does not include passing the information to anyone. This statute offers a year in prison and a fine. https://www.law.cornell.edu/uscode/text/18/1924 (a) Whoever, being an officer, employee, contractor, or consultant of the United States, and, by virtue of his office, employment, position, or contract, becomes possessed of documents or materials containing classified information of the United States, knowingly removes such documents or materials without authority and with the intent to retain such documents or materials at an unauthorized location shall be fined under this title or imprisoned for not more than one year, or both. (b) For purposes of this section, the provision of documents and materials to the Congress shall not constitute an offense under subsection (a). (c) In this section, the term “classified information of the United States” means information originated, owned, or possessed by the United States Government concerning the national defense or foreign relations of the United States that has been determined pursuant to law or Executive order to require protection against unauthorized disclosure in the interests of national security.
Well, Guccifer found some and published them. http://www.thesmokinggun.com/documents/sidney-blumenthal-email-hack-687341 DOCUMENT: Internet, Crime Hacker Targets Clinton Confidant In New Attack Breach exposed e-mails with Hillary Clinton MARCH 15--The hacker who has spent the past several months breaking into the e-mail accounts of family, friends, and political allies of the Bush family has crossed party lines and illegally accessed the AOL account of a former senior White House adviser to President Bill Clinton. The intrusion into Sidney Blumenthal’s e-mail account apparently occurred this week, days after the hacker--who uses the alias “Guccifer”--defaced Colin Powell’s Facebook page and breached the former Secretary of State’s AOL account. The 64-year-old Blumenthal--who was unaware that he had been hacked by “Guccifer”--worked as an assistant and senior adviser to Clinton for about 3-1/2 years, ending in January 2001. He worked as a senior adviser to Hillary Clinton’s 2008 presidential campaign and has remained one of her closest confidants. By breaching Blumenthal’s account, “Guccifer” was able to access his correspondence (dating back to at least 2005) with an array of Washington insiders, including political operatives, journalists, and government officials. As with the hacker’s other victims, it is unclear how Blumenthal’s account was illegally accessed or why he was targeted. However, based on screen grabs made by “Guccifer,” the hacker specifically zeroed in on Blumenthal’s extensive correspondence with Hillary Clinton, sorting Blumenthal’s account so as to single out all e-mail sent to Clinton. Additionally, “Guccifer” further sorted the mail to list (and presumably download) all Word files attached to e-mails sent to Clinton. It is unknown what plans “Guccifer” has for these documents, which include foreign policy and intelligence memos that Blumenthal sent to Clinton while she served as Secretary of State. Blumenthal told TSG that when he attempted to access his e-mail yesterday morning, he could not successfully log in. He then contacted an AOL representative and was told that his account had been compromised. Blumenthal said that he subsequently reset the password and regained control of his account. In e-mail screeds, “Guccifer” seems to subscribe to dark conspiracies involving the Federal Reserve, the Council on Foreign Relations, and attendees of Bohemian Grove retreats. “the evil is leading this fucked up world!!!!!! i tell you this the world of tomorrow will be a world free of illuminati or will be no more,” the hacker declared. Over the past few months, the list of “Guccifer” hacking victims has included several Bush family members and friends; Powell; U.S. Senator Lisa Murkowski; a senior United Nations official; Rockefeller family members; former FBI agents; security contractors in Iraq; a former Secret Service agent; and John Negroponte, a former U.S. ambassador to the United Nations. A majority of these breaches have involved AOL e-mail accounts.
If the government properly and thoroughly investigated the known compromise of documents as it should have done, then it appears impossible that it could have remained unaware of where the Clinton copies resided.
I thought he was accused of passing it to an unauthorized person, even though the mistress herself had a fairly high level of security clearance (and spotless security record) from her own work for the government. Anyway, that's what I've gathered from reading articles. Applying the Petraeus standard to Hitlery will undoubtedly be decried as anti-woman or otherwise evil and retrograde.
Careful or Holder will launch a racism probe against you for asking such uppity questions.
That is correct. That is what he was accused of and would appear to have been guilty of. By his plea agreement, he pleaded guilty as I stated. This should cause great difficulty for Hillary as she surely did as much as what Petraeus pleaded to. Paula Broadwell's security clearance is irrelevant. A security clearance does not permit anyone access to any level of classified information. It only makes them eligible to receive access authorization. Only a grant of access authorization makes one eligible to access classified information. Paula Broadwell did not have it. She did not have a need to know.
Good points. Hopefully Trey Gowdy can pursue it just that straightforwardly. We may be surprised at how interested the libmedia is. They are more Obama drones than Xlinton revanchists. They want to dump Hitlery if they have any other reasonable choice. Like Warren. Or O'Malley in a pinch. Hell, even a Bidenbot has reason to hope Her Thighness will stumble or become discouraged. Breitbart: Top Biden Booster: 'He Ain't Got No Email Problems, He Ain't Got No Foundation Problems'... The public still doesn't understand the wide variety of problems that the Xlinton Foundation has on many fronts. Or just how much the Xlintons are full-blown members of the 1% and Wall Street circles, a group not popular on the Left. A lot of Republicans and conservatives don't follow the internals of the Dems but many of them consider the entire Xlinton reign of terror a waste of time due to Xlinton making compromise deals with Republicans. They want exactly the kind of divisive lawlessness that Obama so uniquely typifies in American politics. Probably the most lawless president on record other than Lincoln.
The news reports are all over the lot, so I obtained the documents from the Court. The charge actually at the Court was the one I quoted, one count 18 U.S.C. § 1924. That is the only charge in the Bill of Information, that he "did unlawfully and knowingly remove such documents and materials without authority and with the intent to retain such documents and materials at unauthorized locations, aware that these locations were unauthorized for the storage and retention of such classified documents and materials. All in violation of Title 18, United States Code, Section 1924." The case is USA v. Petraeus, NCWD 3:15-cr-00047-RJC-DCK-1, date filed 03/03/2015. Of interest is the FACTUAL INFORMATION, created by the government and signed by Petraeus as accurate and correct. Under Criminal Conduct, starting at 6, it relates that Petraeus entered into a Non-Disclosure Agreement (NDA) with the DOD and with the CIA. Basically, when you get a TS clearance and access to specially designated information, you sign an NDA in the process of getting the official access authorization. There should be a similar NDA signed by Hillary Clinton. Paula Broadwell is not referenced by name but only as the DOD biographer of Petraeus. - - - - - US v Petraeus, NCWD 3-15-cr-00047, Doc 1, BILL OF INFORMATION (03 Mar 2015) - - - - - US v Petraeus, NCWD 3-15-cr-00047, Doc 2, PLEA AGREEMENT (03 Mar 2015) - - - - - US v Petraeus, NCWD 3-15-cr-00047, Doc 3, FACTUAL BASIS (03 Mar2015) - - - - -
They apparently had strong evidence that the most top-secret type of information was handled inappropriately. We don't have evidence that Hitlery sent or received comparably sensitive materials on her server. Not to defend her but you have to compare how important and secret the documents are. No doubt about Petraeus, not yet established in the Xlinton case. And a CIA head does have to meet a higher security standard than a mediocre SoS.
#2. To: TooConservative, out damned spot (#1)
#3. To: TooConservative, out damned spot (#1)
Those attachments are very damning.
#4. To: out damned spot, TooConservative (#0)
44 U.S. Code § 3101 - Records management by agency heads; general duties
44 U.S. Code § 3105 - Safeguards
44 U.S. Code § 3106 - Unlawful removal, destruction of records
§ 3101. Records management by agency heads; general duties
§ 3102. Establishment of program of management
§ 3103. Transfer of records to records centers
§ 3104. Certifications and determinations on transferred records
§ 3105. Safeguards
§ 3106. Unlawful removal, destruction of records
§ 3107. Authority of Comptroller General
NARA Bulletin 2011-03
Although e-mail archiving applications may provide business benefits to an agency, e-mail archiving applications can be limited in their capabilities to keep and organize records according to records management laws, regulations, and policies; and,
Provide for the grouping of related records into classifications according to the nature of the business purposes the records serve;
Archivist of the United States
#5. To: nolu chan (#4)

#6. To: A K A Stone, nolu chan (#5)
#7. To: A K A Stone (#5)



Guccifer
#8. To: SOSO, A K A Stone (#6)
Don't get your hopes up. She will look right into the camera a arrogantly state that she did not have sexwill relations with those emails and that she never aksed anyone to lie.
#9. To: nolu chan, A K A Stone (#8)
Hillary ain't Bill.
#10. To: nolu chan (#7)
#11. To: TooConservative, SOSO, A K A Stone (#10)
I want the public to see my email. I asked State to release them. They said they would review them for release as soon as possible.
STORING AND SAFEGUARDING CLASSIFIED MATERIAL 12 FAM 533.2 Certification Upon Permanent Departure from Post
12 FAM 536.1-1 Determination of Trustworthiness
12 FAM 536.1-2 Determination of Need-to-Know
12 FAM 536.2-1 Department of State Records
12 FAM 536.3 Access by Other Persons Outside the Executive Branch
12 FAM 536.6-3 Controls for Dissemination and Use of Intelligence Information
12 FAM 536.8 Personal Use and Conversations
#12. To: nolu chan, TooConservative, A K A Stone, All (#11)
#13. To: TooConservative (#10)
The statute is lacking in serious penalties, it seems.
18 U.S. Code § 1924 - Unauthorized removal and retention of classified documents or material
#14. To: SOSO (#12)
but no-one can find the Sec. of State's emails for years?
March 15, 2013
#15. To: All (#14)
#16. To: nolu chan (#13)
David Petraeus recently pleaded guilty to this criminal offense. Note that what he pleaded guilty to does not include passing the information to anyone. This statute offers a year in prison and a fine.
#17. To: SOSO (#12)
Does anyone else find it bizarre that the Fed can find racist emails in the Ferguson Police Dpet. lickety split but no-one can find the Sec. of State's emails for years?
#18. To: TooConservative (#16)
I thought he was accused of passing it to an unauthorized person, even though the mistress herself had a fairly high level of security clearance (and spotless security record) from her own work for the government.
#19. To: nolu chan (#18)
#20. To: TooConservative (#19)
#21. To: nolu chan (#20)
Top • Page Up • Full Thread • Page Down • Bottom/Latest
[Home] [Headlines] [Latest Articles] [Latest Comments] [Post] [Mail] [Sign-in] [Setup] [Help] [Register]
